(Book) Networking with MikroTik RouterOS: A Practical Approach to Understanding and Implementing RouterOS
Study material for the MTCNA Certification Course, updated to RouterOS v7
In computer networks, visibility is key to understanding and optimizing performance. An essential tool to achieve this visibility is Port Mirroring, also known as SPAN (Switched Port Analyzer) or RSPAN (Remote Switched Port Analyzer).
This technology plays a critical role in monitoring and analyzing network traffic, providing a detailed view of network activity.
At the end of the article you will find a small test that will allow you assess the knowledge acquired in this reading
What is Port Mirroring?
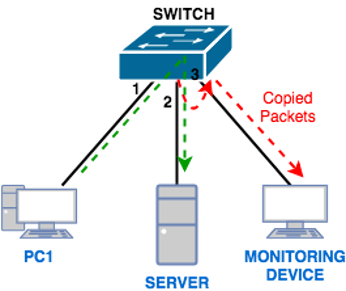
El Port Mirroring is a technique that allows network traffic to be selectively duplicated from a port or multiple ports on a switch and sent to another port for analysis. This makes it easy to monitor traffic without affecting network performance.
The destination port to which mirrored traffic is sent is usually connected to an analysis device, such as a protocol analyzer or network management system (NMS).
On a switch, you choose the ports whose traffic you want to monitor. These ports are known as source ports.
A destination port is designated to which duplicate traffic will be sent. This port is connected to the analysis device.
The switch copies the traffic from the source ports and sends it to the destination port. This allows traffic to flow normally on the source ports while being scanned in parallel on the destination port.
Makes it easy to identify and resolve network problems by providing detailed traffic visibility.
Allows constant monitoring to detect suspicious activities or security threats.
Helps understand network behavior, allowing adjustments to improve performance.
Enables detailed analysis of protocols and applications for informed decision making.
Port Mirroring can place additional load on the switch and network, so it is crucial to efficiently manage resources.
Properly configuring the source and destination ports is essential to ensure the effectiveness of Port Mirroring.
Since Port Mirroring can expose sensitive data, it is vital to implement security measures to protect the privacy of the information.
Wireshark is an open source tool that allows you to capture and analyze network traffic. It is widely used for protocol analysis and troubleshooting.
This software provides comprehensive network monitoring and supports Port Mirroring feature. Offers advanced traffic analysis capabilities.
PRTG is an all-in-one solution that enables network monitoring. You can use port mirroring data to provide detailed traffic reports.
Ntopng is an open source network monitoring tool that provides real-time reports on traffic. It is capable of analyzing traffic captured through Port Mirroring.
Tcpdump is a command line tool for real-time packet analysis. It can be used directly on Unix/Linux systems to examine Port Mirroring traffic.
/interface ethernet switch
set switch1 mirror-source=ether2 mirror-target=ether3
Select a single mirroring source port. Inbound and outbound traffic will be sent to the mirror target port. Note that the mirror destination port must belong to the same switch (see which port belongs to which switch in the /interface ethernet menu).
Select a single destination port for mirroring. Mirrored packets coming from mirror-source.
El Port Mirroring emerges as a valuable tool for network administrators and security professionals.
It provides unprecedented visibility into network traffic, enabling faster problem diagnosis, more effective response to security threats, and continuous optimization of network performance.
However, its implementation must be accompanied by good security and resource management practices to take full advantage of its benefits without compromising the integrity of the network.
Study material for the MTCNA Certification Course, updated to RouterOS v7
Study material for the MTCNA Certification Course, updated to RouterOS v7
Av. Juan T. Marengo and J. Orrantia
Professional Center Building, Office 507
Guayaquil. Ecuador
Zip Code 090505
to our weekly newsletters
Copyright © 2024 abcxperts.com – All Rights Reserved
Take advantage of the Three Kings Day discount code!
Take advantage of the New Year's Eve discount code!
Take advantage of the discount code for Christmas!!!
all MikroTik OnLine courses
all Academy courses
all MikroTik Books and Book Packs
Take advantage of the discount codes for Cyber Week!!!
all MikroTik OnLine courses
all Academy courses
all MikroTik Books and Book Packs
Take advantage of the discount codes for Black Friday!!!
**Codes are applied in the shopping cart
Take advantage of discount codes for Halloween.
Codes are applied in the shopping cart
11% discount on all MikroTik OnLine courses
11%
30% discount on all Academy courses
30%
25% discount on all MikroTik Books and Book Packs
25%