IPv6 book with MikroTik, RouterOS v7
Study material for the MTCIPv6E Certification Course updated to RouterOS v7
The fragmentation extension header in IPv6 is used when a packet exceeds the maximum transmission size (MTU) of a link along the delivery path. Fragmentation splits the original packet into smaller fragments that can be transmitted over the link without exceeding the MTU.
At the end of the article you will find a small test that will allow you assess the knowledge acquired in this reading
When an IPv6 packet is fragmented, the fragmentation header is added to the beginning of each generated fragment. The fragments are transmitted individually over the network and then reassembled at the destination node.
It is important to note that fragmentation in IPv6 is not as common as in IPv4. In IPv6, fragmentation-free routing is preferred whenever possible. This means that nodes and routers along the path must be configured to handle full MTU size packets and not fragment them.
If a packet exceeds the MTU on a link, the source node should attempt to discover an alternative path or use MTU discovery techniques to avoid fragmentation.
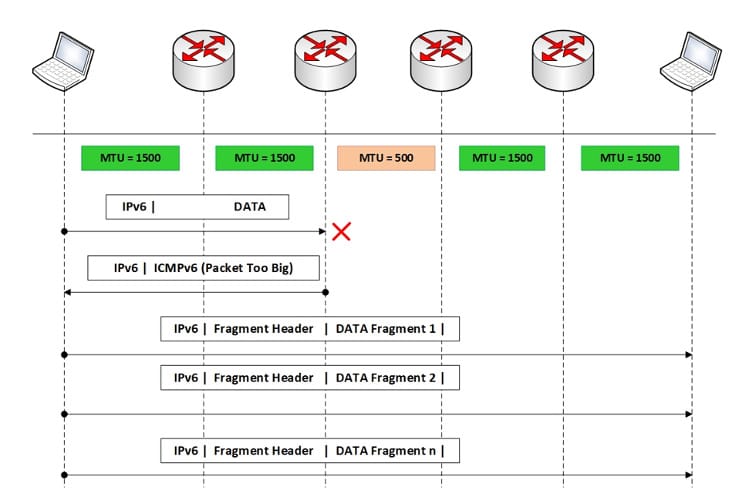
Among the most important aspects of fragmentation we can detail the following:
In IPv6, fragmentation is usually performed at the source node when a packet is generated that exceeds the MTU of the outgoing link. The source node splits the packet into smaller fragments and adds the fragmentation extension header to each fragment.
Each fragment has its own fragmentation header with information such as the Fragment Offset and the More Fragments flag.
Unlike IPv4, where routers can fragment packets in transit, in IPv6 routers are not allowed to fragment packets. This is known as “fragmentation-free routing.” Routers simply drop IPv6 packets that exceed the MTU of the link instead of fragmenting them. This reduces the processing load on routers and improves network efficiency.
Reassembly of the fragments is performed on the destination node. The destination node uses the packet ID and the Fragment Offset field to collect the related fragments and reassemble the original packet. The More Fragments flag is used to determine when the last fragment has been received and reassembly can be completed.
If an IPv6 packet needs to pass over links with different MTUs, chain fragmentation can occur. In this case, the source node will fragment the original packet into fragments that fit the MTU of each link along the path. Routers will then only forward the fragments without performing additional fragmentation.
IPv6 also includes a fragmentation option called the “Jumbo Payload Option.” This option is used to send packets that exceed the maximum size allowed by the MTU of most links. The Jumbo payload option allows packets up to 4 GB in size to be fragmented and reassembled.
Fragmentation in IPv6 can affect quality of service. When fragmenting a packet, some of the quality of service information that was present in the original packet may be lost. This can cause degradation in performance and prioritization of fragments during reassembly on the destination node.
To avoid fragmentation in IPv6, the Path MTU Discovery mechanism is used. PMTUD allows source nodes to adjust packet sizes along the delivery path using the lowest MTU found. This prevents fragmentation and ensures efficient transmission without packet loss.
Fragmentation in IPv6 can introduce some limitations and problems in the network:
Keep in mind that, although fragmentation in IPv6 is possible, it is recommended to avoid it whenever possible. Fragmentation-free routing and proper use of MTU discovery are critical to ensuring optimal performance and minimizing complexity in the network.
The Authentication extension header provides a mechanism for authentication and integrity verification of IPv6 packets. This header is placed after the IPv6 extension header and before the payload header. Its main purpose is to ensure that the origin and/or content of the packet have not been altered during transmission.
The authentication process in IPv6 with the Authentication extension header involves the source of the packet generating a digital signature or message authentication code using a shared secret key or an asymmetric key. The receiver of the packet can verify the authenticity and integrity of the packet using the same key.
The Authentication extension header can be used in different scenarios and applications that require a high level of security and authentication. Below are some cases where this header can be used:
Importantly, use of the Authentication extension header requires an appropriate key management mechanism and security infrastructure. Additionally, both the source and the receiver must be able to perform the necessary authentication operations and share the corresponding secret or public key.
The extension header Encapsulation Security Payload (ESP) It is used to provide security services, such as confidentiality, integrity, and authentication, to IPv6 packets. The ESP header is placed after the IPv6 extension header and before the packet payload. Its main purpose is to protect the packet data from unauthorized access and tampering during transmission.
The ESP extension header allows the source and destination systems to negotiate the cryptographic algorithms and security parameters used to protect the communication. Systems can agree to use symmetric or asymmetric encryption, as well as authenticate messages using cryptographic hash functions.
Using the ESP extension header allows you to secure sensitive communications, protect data privacy, and prevent eavesdropping and tampering attacks. However, its implementation requires proper configuration and administration, including establishing and managing encryption and authentication keys.
This header has the following characteristics:
Study material for the MTCIPv6E Certification Course updated to RouterOS v7
Av. Juan T. Marengo and J. Orrantia
Professional Center Building, Office 507
Guayaquil. Ecuador
Zip Code 090505
to our weekly newsletters
Copyright © 2024 abcxperts.com – All Rights Reserved
40% discount on MikroTik books and book packs - Discount Code: AN24-LIB Discard
Take advantage of the Three Kings Day discount code!
Take advantage of the New Year's Eve discount code!
Take advantage of the discount code for Christmas!!!
all MikroTik OnLine courses
all Academy courses
all MikroTik Books and Book Packs
Take advantage of the discount codes for Cyber Week!!!
all MikroTik OnLine courses
all Academy courses
all MikroTik Books and Book Packs
Take advantage of the discount codes for Black Friday!!!
**Codes are applied in the shopping cart
Take advantage of discount codes for Halloween.
Codes are applied in the shopping cart
11% discount on all MikroTik OnLine courses
11%
30% discount on all Academy courses
30%
25% discount on all MikroTik Books and Book Packs
25%