Most common searches
Mikrotikfirewallvpnnetinstallhome ap
Chapter 3.4 – Firewall Filter
Structure: chains and actions
- A chain: is a grouping of rules based on the same criteria. There are three default chains based on predefined criteria.
- input: The traffic going to the router
- forward: The traffic that goes through the router
- output: Traffic coming from the router
- For example, you can implement a chain passed in:
- Based on criteria: all icmp traffic.
- Based on traffic coming from Ethernet ports, for example: Ether2 towards a remote LAN network or a bridge network.
- Users define the chains, and these are created depending on the parameters that can be compared, and if they wish they can make a "jump" so that once the match has been confirmed, a jump will be made to another rule in the firewall, This is defined in "jump target"
- An action dictates what the filter or rule will do when packets meet all the conditions to be filtered.
- Packets are checked sequentially against existing rules in the current firewall chain until a match occurs. (When you have the # it means that it will respect an order: first one if they match, the action is applied, and from there it will go to the next if that option is enabled, otherwise the analysis will end there)
Firewall filtering in action
You can take advantage of the security of a firewall in different ways such as:
- Trust in the security of our LAN, since what comes from the WAN is insecure.
- We block everyone and allow only what we agree on.
- We will allow everything and block only what causes problems.
Basic Tips and Tricks
- Before making changes to the firewall, let's enter "safe mode"
- After making configurations and changes to firewall rules, it is advisable to test for weaknesses: a recommended tool: ShieldsUP
- Before starting, it is recommended to write in plain text or on paper a simple description of the policies you want to apply.
- Once you understand them and agree with them, you proceed to log in to the router.
- Add the following rules progressively, once you are satisfied with the basic rules entered.
- If you are new to the security area, it is advisable not to enter rules that point in all directions, it is enough to do the basics, but you have to do it well.
- It's a good idea to end your chains with catch-all rules and see what you may have missed.
- You will need two catch-all rules, one log and one drop for all unprecedented traffic. Both should be based on the same compared parameters for it to be useful to you.
- Once you see what makes it to the catch-all rules, you can add new rules based on the behavior desired by the firewall.
Filtering by Parameters (Filter Actions)
Before deciding to take action on the firewall, you must first identify it. We have many parameters by which we can compare.
Once the match has been made with all the parameters of a rule, and they match, then an action will be performed. MikroTik firewall has the following 10 actions:
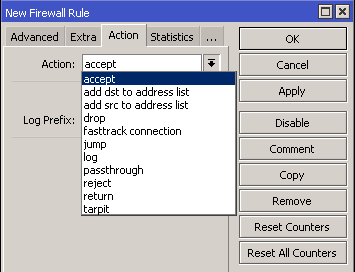
- accept: Accept the package. The Packet would no longer be passed to the next firewall rule.
- add-dst-to-address-list: destination address, after matching the packet goes to the next rule.
- add-src-to-address-list: source address. After matching the packet goes to the next rule.
- drop: the packet is discarded. After matching the packet goes to the next rule.
- jump: jump is defined by the user and is used to jump to a specific rule, defined by the jump-target. After matching the packet goes to the next rule defined in jump-target.
- log: Adds a message to the logs with the following information: in-interface, out-interface, src-mac, protocol, src-ip:port->dst-ip:port and length of the packet. After matching the packet goes to the next rule.
- passthrough- If this option is checked, it will enable the option to ignore subtract rule and move to the next (very useful for network statistics).
- reject- Discards the icmp packets and sends a user-defined message the packet is not passed to the next rule.
- return- Passes control of the filter again, where the previous filter originated. After matching the packet goes to the next rule (only if the previous rule does not cause the packet to be discarded and stop the match).
- tarpit- Captures and retains TCP packets (replicas with SYN/ACK for incoming TCP SYN packets). After matching the packet goes to the next rule.
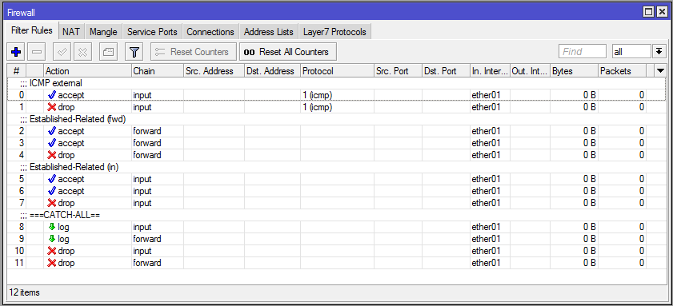
Protecting your router (input)
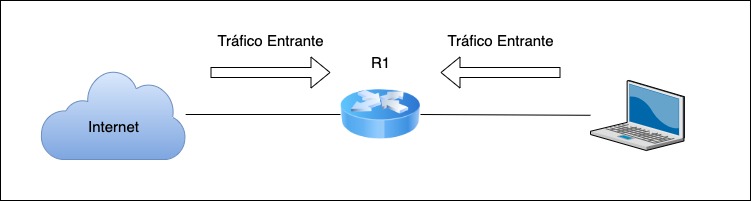
- El chain=input analyzes all incoming traffic to the router.
- When applying a rule chain=input, the entry of information to the router is controlled
MikroTik gives the following suggestions for Input
Assuming the ether1 interface is connected to an insecure WAN.
- Accept traffic from icmp-echo-reply (if you want to have a ping replica over the internet, this is useful when we manage servers)
- Discard all icmp-echo-request traffic (When we do not want another device to ping us. With this we avoid being targeted by attacks such as smurf attacks or others)
- Accept all established and related incoming traffic.
- Drop all invalid traffic.
- Log all other traffic
- Discard all other traffic.
Protecting all customers (forward)
Forward traffic is the traffic that passes through the router.
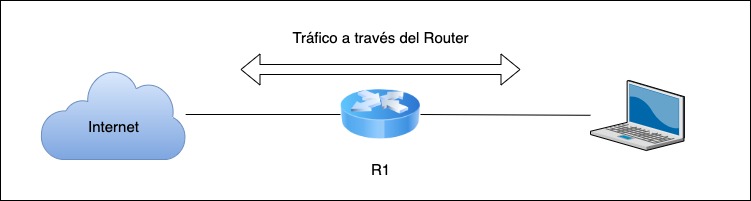
MikroTik gives the following suggestions for the Forward
Assuming the ether1 interface is connected to an insecure WAN.
- Accept all established and related forward traffic.
- Drop all invalid traffic.
- Log all other traffic (to verify if any important packets have been blocked)
- Discard all other traffic.
- Share this Article
Facebook
Twitter
LinkedIn
WhatsApp
Telegram
Other documents in this category
Tutorials available at MikroLABs
No Courses Found!