(Book) Networking with MikroTik RouterOS: A Practical Approach to Understanding and Implementing RouterOS
Study material for the MTCNA Certification Course, updated to RouterOS v7
Using shared keys for wireless authentication is a method used on Wi-Fi networks to verify the identity of devices trying to connect to a network.
This method is based on the shared knowledge of a secret key between the device requesting the connection (client) and the access point (AP) or router.
At the end of the article you will find a small test that will allow you assess the knowledge acquired in this reading
Here is a detailed explanation of how this process works:
Before any authentication can take place, both the access point (AP) and client devices must have the same shared key configured.
This key is established by the network administrator and must be entered manually in the AP configurations and in each of the devices that wish to connect to the network.
The Shared Key Authentication process typically follows these steps:
Although authentication using shared keys may seem secure, it has several vulnerabilities:
Due to these vulnerabilities, the use of shared keys for wireless authentication has largely been replaced by more secure methods, such as WPA2 (Wi-Fi Protected Access 2) and WPA3, which use more robust authentication protocols such as EAP (Extensible Authentication Protocol) along with a variety of encryption methods to protect wireless communications.
Although shared key authentication was one of the first methods used in Wi-Fi networks, its security limitations have led to the adoption of more advanced and secure authentication and encryption technologies.
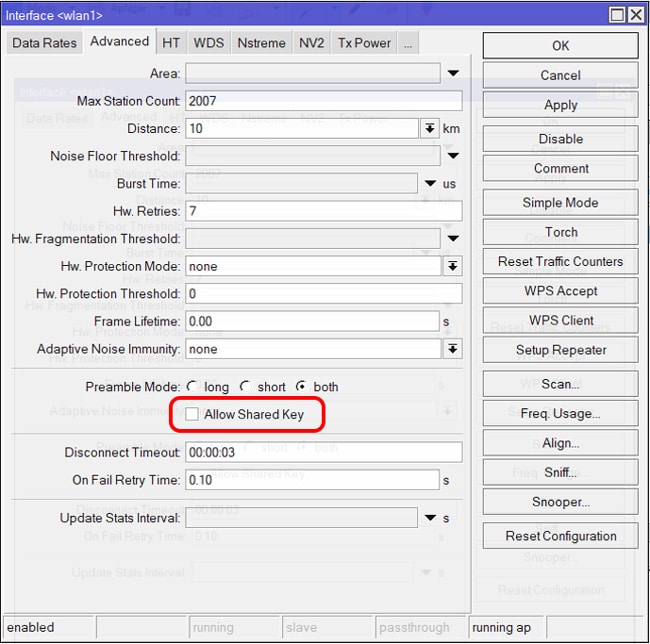
The allow-shared-key option in MikroTik RouterOS is a setting that allows or disallows the use of shared keys for wireless authentication. Shared keys, also known as WEP, are a type of older wireless network encryption that is considered insecure.
The “Allow Shared Key” option is relevant when configuring wireless security on a MikroTik access point and refers to whether or not to allow shared key authentication in the context of WEP or WPA. However, it is recommended to use more advanced and secure security methods whenever possible.
WEP (Wi-Fi Protected Access) It is the first Wi-Fi security protocol. It uses RC4 encryption, which is a relatively weak stream cipher algorithm. 64-bit WEP keys can be cracked in a matter of minutes, and 128-bit or 256-bit keys can be cracked in a few hours.
WPA (Wi-Fi Protected Access) is an enhancement to WEP that uses TKIP (Temporal Key Integrity Protocol) encryption. TKIP is a stronger encryption algorithm than RC4, but it is still susceptible to attacks.
WPA2 (Wi-Fi Protected Access 2) It is the most recent version of the Wi-Fi security protocol. It uses AES (Advanced Encryption Standard) encryption, which is the strongest encryption algorithm available for Wi-Fi. WPA2 is much more secure than WEP or WPA, and is very difficult to crack.
In general, it is recommended to use WPA2 to protect your wireless network. It is the most secure security protocol available and is supported by most modern wireless devices.
Feature | WEP | WPA | WPA2 |
Encryption | RC4 | TKIP or AES | BEA |
Key length | 64, 128 or 256 bits | 80 or 128 bit | 128 or 256 bit |
Security | Unsafe | More secure than WEP | More secure than WPA |
Compatibility | Wide | Wide | Wide |
Configuration difficulty | Easy | Easy | Easy |
Bandwidth requirements | Altos | Media coverage | Media coverage |
Study material for the MTCNA Certification Course, updated to RouterOS v7
Study material for the MTCNA Certification Course, updated to RouterOS v7
Av. Juan T. Marengo and J. Orrantia
Professional Center Building, Office 507
Guayaquil. Ecuador
Zip Code 090505
to our weekly newsletters
Copyright © 2024 abcxperts.com – All Rights Reserved
40% discount on MikroTik books and book packs - Discount Code: AN24-LIB Discard
Take advantage of the Three Kings Day discount code!
Take advantage of the New Year's Eve discount code!
Take advantage of the discount code for Christmas!!!
all MikroTik OnLine courses
all Academy courses
all MikroTik Books and Book Packs
Take advantage of the discount codes for Cyber Week!!!
all MikroTik OnLine courses
all Academy courses
all MikroTik Books and Book Packs
Take advantage of the discount codes for Black Friday!!!
**Codes are applied in the shopping cart
Take advantage of discount codes for Halloween.
Codes are applied in the shopping cart
11% discount on all MikroTik OnLine courses
11%
30% discount on all Academy courses
30%
25% discount on all MikroTik Books and Book Packs
25%